Security Monitoring and Observability
Gain visibility into your organization's security posture
Gain visibility across your environments to reduce the mean time needed to detect, alert, and remediate security incidents with Security Observability
Single source of truth
Simplify business-critical decision-making based on deeper visibility to system health and security integrity.
Proactive approach
Quickly identify, analyze, and categorize suspicious patterns and anomalies.
Eliminate complexities
Gain insights into the entire internal state of a complex IT distributed system or environment.
Less alert fatigue and silos
Reduce alert fatigue and help eliminate internal silos in both on-prem and hybrid environments and provide an understanding of interdependencies.
Gain visibility into security events across networks, infrastructures, applications, and databases.
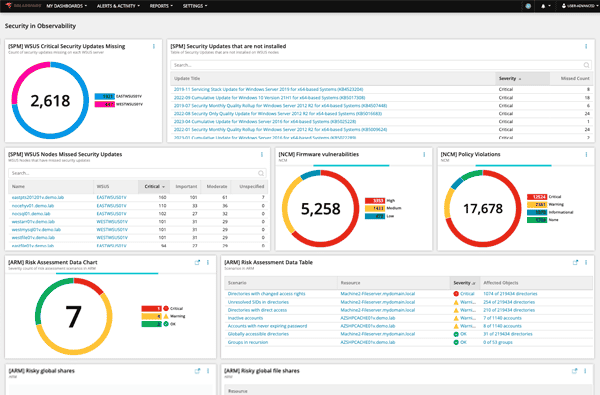
Vulnerability and risk dashboard
Introducing our latest dashboard that enables customers to identify risks in their environment based on vulnerabilities. Vulnerability information is available for Cisco, Juniper, Windows, Linux, and VMware devices.
Security summary dashboard
Our Security Summary Dashboard solution offers a unified dashboard for visibility into security events across networks, infrastructures, applications, and databases. It provides a powerful way to monitor your security and regulatory compliance status on a dedicated security dashboard with summary widgets from Security Event Manager (SEM), Access Rights Manager (ARM), and Patch Manager.
SEM summary dashboard
This dashboard displays widgets based on SEM-saved queries, which are scheduled to execute at any frequency and with tags. For each of these queries, you can set minimum or maximum thresholds to determine the severity level of these queries.
Our security solutions are built to improve IT security and compliance teams' agility, flexibility, and effectiveness
Self-hosted observability to take you from reactive to proactive across on-prem and hybrid IT environments.
- Deployment to meet your needs, whether behind your firewall or self-hosted in AWS®, Microsoft® Azure, or GCP®
- Flexible licensing – allocate nodes across multiple instances – and optimal scalability
- Built from our years of network management leadership and enhanced with machine learning
Manage and audit access rights across your IT infrastructure
- Rapidly identify and reduce the risk of unauthorized system access and data breaches
- Easily create user accounts and review user permissions, groups, and access across all systems and data
- Help demonstrate compliance with reports
Improve your security posture and quickly demonstrate compliance with an easy-to-use, affordable SIEM tool
- Centralized log collection and retention
- Automated threat detection and response
- Integrated compliance reporting tool
Ready to experience complete monitoring and observability built on decades of experience?
You may still have questions. We definitely have answers.